1. Sysdig Secure
Sysdig secure receive immediate vulnerability alerts through customizable policy-based notifications. For near real-time alerts on your runtime workloads or CI/CD pipelines, connect your Vulnerability Management (VM) policies to Slack, PagerDuty, Teams, Amazon SNS, or your preferred channel. Customize your notifications with care; you are the sole individual capable of preventing the occurrence of another muted Slack channel.
Two new features, CMD Overlay and Network Tables, allow you to delve deeper into your environment. Focus on the precise commands that were executed and their locations with granular Activity Audit filtering. Subsequently, reveal the specifics of each network request to obtain a comprehensive understanding. Feel free to examine it more closely.

2. Sysdig CLI Scanner
Sysdig is delighted to announce a significant improvement to the sysdig-cli-scanner utility, which now includes Infrastructure as Code (IaC) scanning capabilities. This release enhances the security posture of your development workflows by enabling users to seamlessly scan IaC resources for potential hazards and compliance issues. To identify potential risks and compliance issues early in the development lifecycle, you can initiate IaC assessments using the familiar sysdig-cli-scanner interface. The fundamental functionality is still being supported by the instrument.
- A comprehensive exit code system that facilitates the interpretation of scan results.
- The implementation of role-based access control (RBAC) to ensure the precise management of permissions
- Cross-platform compatibility
- Ability to integrate into existing workflows, such as CI/CD pipelines
- Consistency with the VM CLI is guaranteed through the utilization of API tokens for authentication.
- Command execution that is straightforward
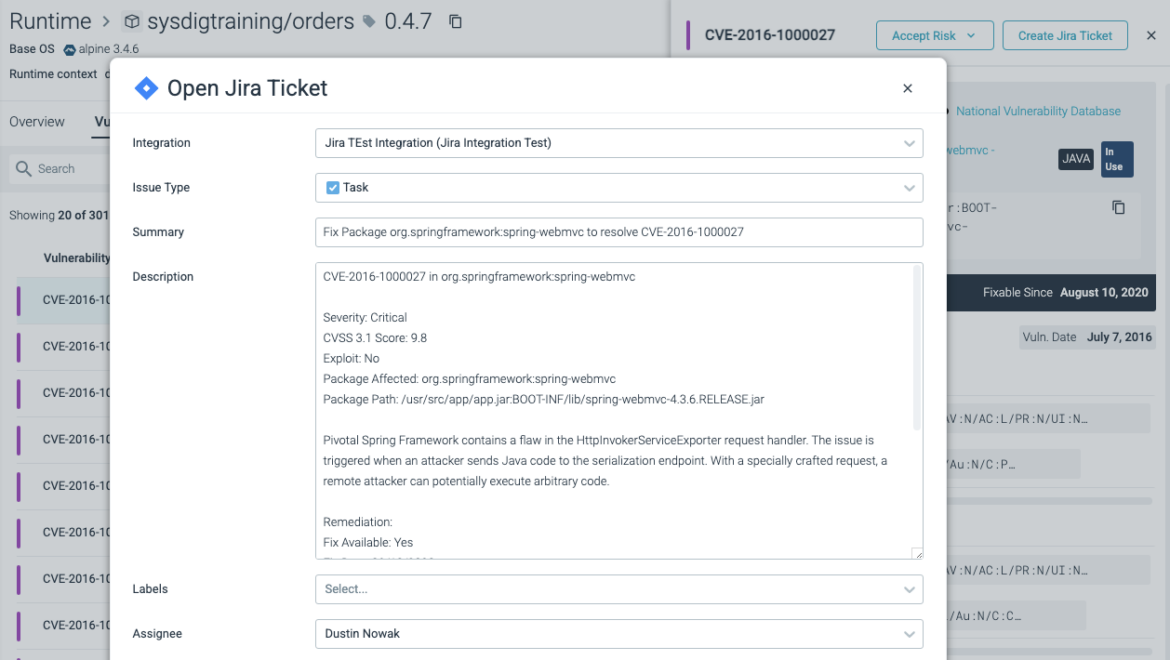
3. Vulnerability Management (VM) has now been fully integrated with Jira
Jira has been completely integrated with Vulnerability Management (VM). To generate a fully-fleshed-out Jira ticket, simply click on any vulnerability in the VM module. From the Sysdig UI, you can designate the ticket to a colleague. Subsequently, Sysdig will retain which vulnerabilities have Jira requests.
Read :Top 5 Reasons Why Sysdig Is Used by Goldman Sachs
4. Sysdig Monitor
Sysdig Monitor now provides an even greater number of alerts that are actionable. Crucial contextual identifiers, including host_hostname, cloud_provider_region, and kube_cluster_name, are automatically included in the notification when an alert rule is triggered. This surpasses the capabilities of OSS Prometheus by providing detailed information that facilitates the rapid identification and resolution of Metric and PromQL alerts. In situations where pricing information is unavailable, such as when observing on-premises Kubernetes clusters, Cost Advisor will now employ Sysdig Default prices. Furthermore, Cost Advisor has been improved to assist you in determining the invoicing profile that is linked to a particular Kubernetes cluster.
A visual snapshot of the time series data that initiated the alert rule will now be included in the Alert Notifications sent to Slack, email, and Pagerduty. This entails a reduction in dashboard searching at 2 a.m. and the capacity to escalate or snooze without requiring the use of a laptop.
5. Sysdig Agents
Sysdig Agent 12.20.0: Streamlined Configuration and Optimized Performance
Our latest update brought several improvements to the Sysdig Agent, focusing on easier setup and enhanced handling of demanding workloads.
Simplified Runtime Detection Configuration
We’ve removed the sysdig_secure.enabled tag for a cleaner configuration process. To check if runtime detection is enabled, simply look for the agent_secure_enabled label in the sysdig_agent_info metric.
Adaptive Kernel Sampling
The agent now responds more effectively to high event loads. This optimization means smoother performance and more reliable insights, even during busy periods.
Container Actions and Captures
Extend your security toolkit with new actions in Container Drift and Malware policies. You now have the ability to:
- Create capture files for in-depth analysis
- Kill, Pause, or Stop containers in response to threats
6. Improved GCP Cloud Account Onboarding
Sysdig has implemented an enhanced enrollment experience for GCP Cloud Accounts. Users have the ability to specify their installation preferences with respect to their desired features. The installation process is subsequently guided by Sysdig, ensuring a personalized and seamless experience each step of the way. Furthermore, threat detection on GCP is now supported by Sysdig’s Agentless CDR. Users can effortlessly connect their GCP accounts and enjoy comprehensive event processing by utilizing Falco and its constantly updated rules, which are managed by the Sysdig Threat Research Team, as well as custom rules that are customized to specific environments and security requirements.
7. Improved Azure Cloud Account onboarding
Sysdig has implemented an enhanced enrollment experience for Azure Cloud Accounts. Users have the ability to specify their installation preferences with respect to their desired features. The installation process is subsequently guided by Sysdig, ensuring a personalized and seamless experience each step of the way. Furthermore, Azure threat detection is now supported by Sysdig’s Agentless CDR. Users can effortlessly connect their Azure accounts and enjoy comprehensive event processing by utilizing Falco and its constantly updated rules, which are managed by the Sysdig Threat Research Team, as well as custom rules that are customized to specific environments and security requirements.
8. Sysdig Cluster Shield released as controlled availability
Sysdig is thrilled to announce the controlled availability of Sysdig Cluster Shield. By consolidating numerous agent deployments into a single containerized component, this solution simplifies the deployment, management, and configuration of the Sysdig suite of security and compliance tools at the cluster level. This represents a substantial improvement. Cluster Shield simplifies the process of maintaining your security and compliance posture in Kubernetes environments by optimizing operations.
9. Sysdig eBPF architecture
The architecture of Sysdig with eBPF looks like this:
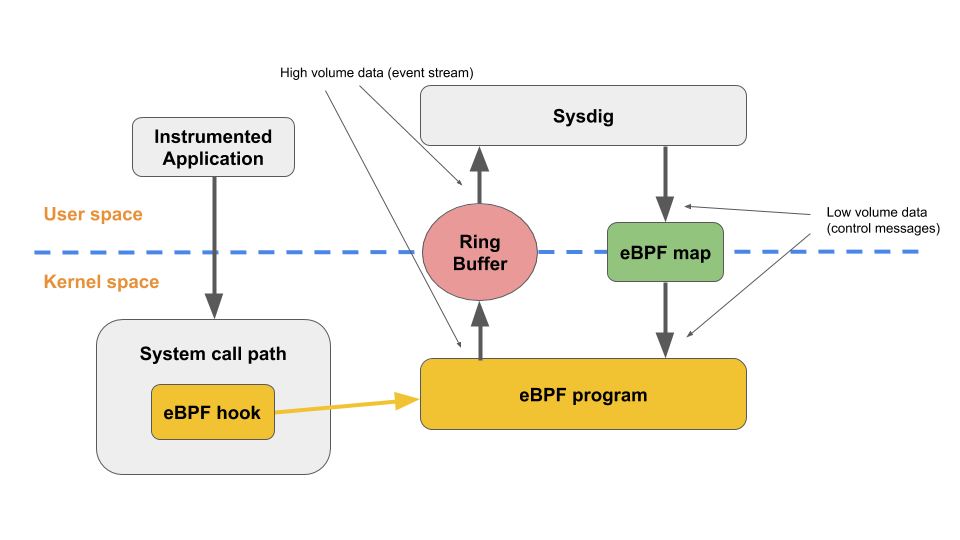
At the heart of the implementation is a collection of custom eBPF programs that are responsible for the instrumentation. As previously mentioned, these programs are composed in a subset of the C programming language. They are compiled using the most recent versions of LLVM and Clang, which translate the high-level C code into the eBPF bytecode. Each execution point where Sysdig instruments the kernel has a unique eBPF program. At present, Sysdig associates eBPF programs with the subsequent static tracepoints:
- System call entry path
- System call exit path
- Process context switch
- Process termination
- Minor and major page faults
- Process signal delivery
10. Kubernetes 1.31
37 line items are tracked as “Graduating” in Kubernetes 1.31, which introduces a plethora of enhancements. From these, 11 enhancements are transitioning to stable, including the eagerly awaited AppArmor support for Kubernetes. This feature enables the specification of an AppArmor profile for a container or pod in the API, and the container runtime will apply the profile. At the same time, 34 new alpha features are being introduced, with a significant focus on the initial design to accommodate pod-level resource limitations. This progress will be of particular interest to security personnel.
Be on the lookout for significant changes, such as the enhanced connectivity reliability of KubeProxy Ingress, which now provides a more effective connection draining capability on terminating Nodes, and for load balancers that support this feature. In order to further improve security, we anticipate that pod-level resource limits will transition from Net New to Alpha. This will provide a feature that is comparable to Resource Constraints in Kubernetes, which harmoniously balances operational efficiency with comprehensive security. Additionally, there are numerous enhancements to the quality of life that contribute to the ongoing trend of enhancing the efficiency and user-friendliness of Kubernetes. For instance, a randomized algorithm is implemented to select pods during the downscaling of ReplicaSets.
Read: Top 5 Strategies for Cloud Security Regulations in Financial Services by Sysdig
To share your insights with the FinTech Newsroom, please write to us at news@intentamplify.com








